Your Next Qi Wireless Charger Design Needs Secure Authentication
Why do wireless chargers need secure authentication? The simple answer is that the Qi v1.3 from the Wireless Power Consortium (WPC) mandates it because unsecured wireless chargers not only present a security threat, but can also compromise the user experience and safety. For example, a device may charge too slowly or too fast and overheat (or worse, catch fire), or battery damage may occur due to poorly regulated charging algorithms.
Regarding cyber security, identified attack vectors include side-channel attacks1 and hijacking and eavesdropping attacks2. These can be used by ‘evil’ chargers someone might use in public spaces that would enable the charger to access data on the phone or simply disrupt its operation.
The WPC is determined to tackle the security, user experience, and safety issues head-on. Now, if a user has a mobile phone or other device designed to the new Qi v1.3 standard, it must be charged with a Qi v1.3 charger, or it may not charge. And if it charges at all, it can be limited to the slowest charging rate. To ensure this, Qi v1.3 mandates that a private key be stored and protected by a certified secure storage subsystem (SSS) in the charger, including X.509 certificates, to verify the charging source cryptographically.
When the device is placed on the charger, it will request security certification. Without an authenticated private key from the charger, the device may reject the charger. Bottom line: old devices will work with the new standard, but Qi v1.3 devices may not work with older chargers (Figure 1).
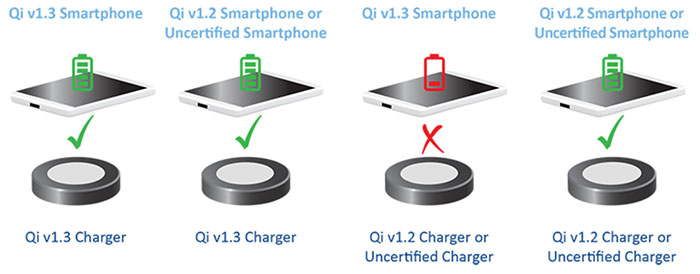 Figure 1: Devices using the new Qi v1.3 standard are not expected to work with uncertified chargers or chargers using earlier versions of the Qi standard. (Image source: Microchip Technology
Figure 1: Devices using the new Qi v1.3 standard are not expected to work with uncertified chargers or chargers using earlier versions of the Qi standard. (Image source: Microchip Technology
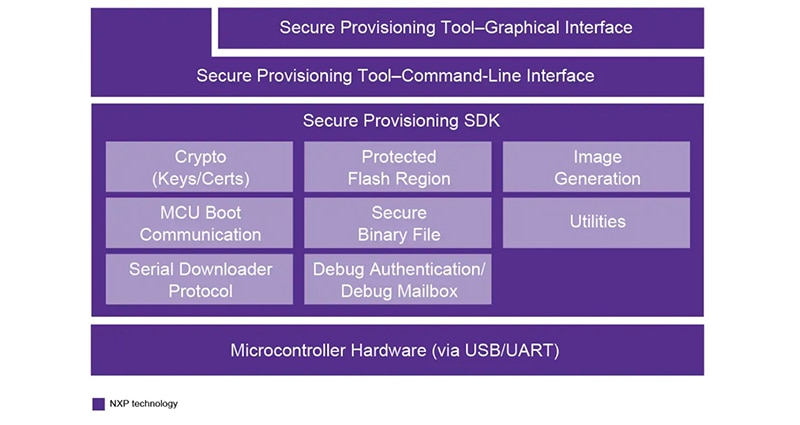
To remove any exposure of the private keys and support the chain of trust, all private keys involved must be in an SSS in the charger. The WPC mandates three steps to ensure the chain of trust of the private keys (Figure 2):
- The third-party root certificate authority (CA) creates a root certificate and its associated root private key that signs the manufacturer certificate signing request (CSR). The manufacturer certificate is unique to each wireless charger company, and the product certificate is unique to every charger.
- The manufacturer CA (MFG Cert) creates the manufacturer certificate and protects its associated private key in a certified SSS.
- The needed public/private key pair for product certification is generated and protected during the manufacturing of the SSS. The private key is provisioned inside the SSS within the charger, and the SSS sends a CSR to the manufacturing CA that is already signed by the root certificate.
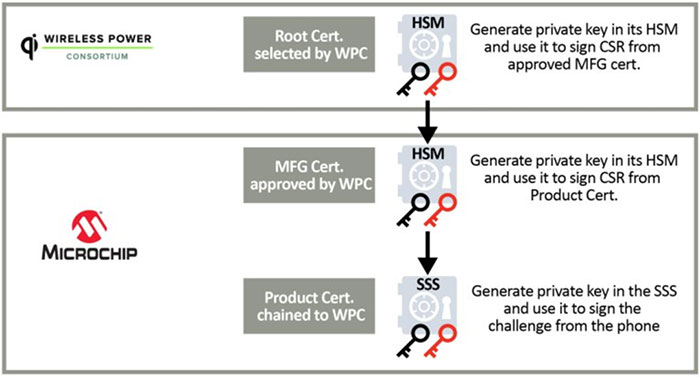 Figure 2: Three steps are used to ensure the chain of trust of the private keys within the SSS and used for secure authentication. (Image source: Microchip Technology)
Figure 2: Three steps are used to ensure the chain of trust of the private keys within the SSS and used for secure authentication. (Image source: Microchip Technology)
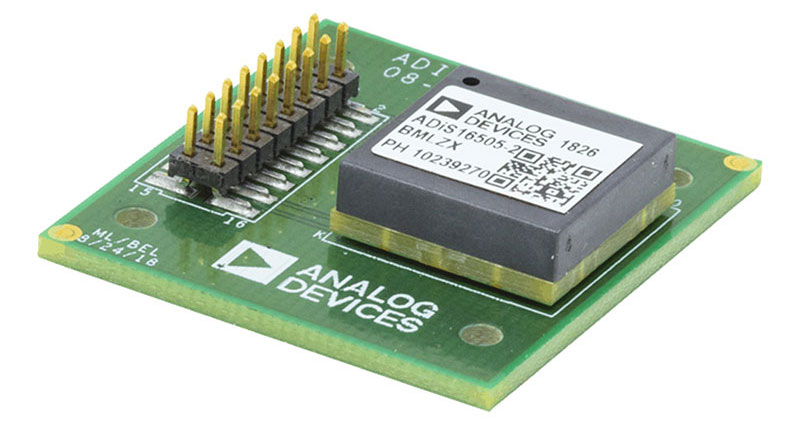
Designers of wireless chargers can use the ECC608-TFLXWPC from Microchip as a pre-provisioned secure element that meets the secure authentication requirements mandated by Qi v1.3 (Figure 3). In addition to supporting Qi v1.3 secure authentication, it supports code authentication (secure boot), message authentication code (MAC) generation, trusted firmware updates, multiple key management protocols, and other root-of-trust-based operations. It’s designed to provide security services for a microcontroller (MCU) or microprocessor (MPU) in the charger.
 Figure 3: The ECC608-TFLXWPC is a pre-provisioned secure element that meets the secure authentication requirements mandated by Qi v1.3. (Image source: Microchip Technology)
Figure 3: The ECC608-TFLXWPC is a pre-provisioned secure element that meets the secure authentication requirements mandated by Qi v1.3. (Image source: Microchip Technology)
To get you started, the CryptoAuthentication SOIC Xplained Pro Starter kit includes a SAMD21-XPRO and an AT88CKSCKTSOIC-XPRO socket board along with Crypto Authentication sample devices. The starter kit works with Microchip Technology's CAL Library and CAL Python tools; by setting the needed switches on the socket board, it can support I2C, single-wire interface (SWI), and SPI interface devices.
 Figure 4: The CryptoAuthentication SOIC Xplained Pro starter kit includes a SAMD21-XPRO (blue board) and an AT88CKSCKTSOIC-XPRO socket board (red board) along with sample devices. (Image source: Microchip Technology)
Figure 4: The CryptoAuthentication SOIC Xplained Pro starter kit includes a SAMD21-XPRO (blue board) and an AT88CKSCKTSOIC-XPRO socket board (red board) along with sample devices. (Image source: Microchip Technology)
Conclusion
Wireless chargers designed to the new Qi v1.3 standard must include secure authentication using a mandated chain of trust to ensure good user experiences and safety—in addition to protection from cyberattacks. Devices like mobile phones that meet the earlier Qi standards can be charged with a charger built to the v1.3 standard, but devices built to the v1.3 standard cannot be guaranteed to work with older chargers. This puts the onus on designers to get Qi V1.3 implemented quickly. As shown, there are ICs and development kits already emerging and available to move Qi v1.3 development forward.
Recommended Reading
The Anatomy of Security Microcontrollers for IoT Applications
What’s Good Enough When It Comes to Security?
References:
1: Wireless Charging Power Side-Channel Attacks
Cornell University
Association for Computing Machinery

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum