Tighten Security with Secure Provisioning
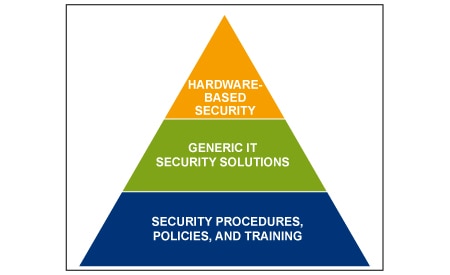
Security keys form the bedrock of a system’s security foundation and protecting private keys and other secrets is one of the most important requirements for any connected device. Unfortunately, even if you shield your security keys under layers of protection in your designs, lax security when finally loading keys and firmware during production can undermine the most careful preparations.
Well-documented attacks on connected systems and infrastructure have cast a spotlight on underlying security vulnerabilities that can arise in creating complex operational technology (OT) solutions. In critical applications like healthcare, industrial, transportation, and energy, successful penetration of security measures not only exposes sensitive data but also compromises safe execution of the application itself.
As consumers fill their homes and offices with Internet of Things (IoT) devices, breakdowns in device security become more personal. It’s no surprise that device designers have continually listed security implementation as one of their top development concerns.
The good news is, solutions are available.
Secure devices and kits
The availability of specialized security chips and security-enabled processors has significantly simplified device security implementation. Perhaps even better, their hardware-based execution of cryptographic algorithms prevents attacks on software-based security mechanisms that have plagued more traditional systems. Most of these chips and processors incorporate hardware-based secure key storage and build on those protected keys to offer a hardware root of trust needed to ensure end-to-end security. Yet, the process of loading (or “provisioning”) keys into those hardware devices often puts humans in the loop, potentially exposing secrets through accident or intention, providing an opening that hackers can exploit using the kind of social engineering attacks that remain so effective.
Many semiconductor manufacturers and distributors provide a secure provisioning service that performs this critical step using hardware security modules (HSM) designed with safeguards to protect against physical or electronic intrusion. However, factory provisioning isn’t always available or not suitable due to internal requirements, and IoT device developers face the additional challenge of securely loading trusted firmware into their devices. Fortunately, some alternative solutions are available.
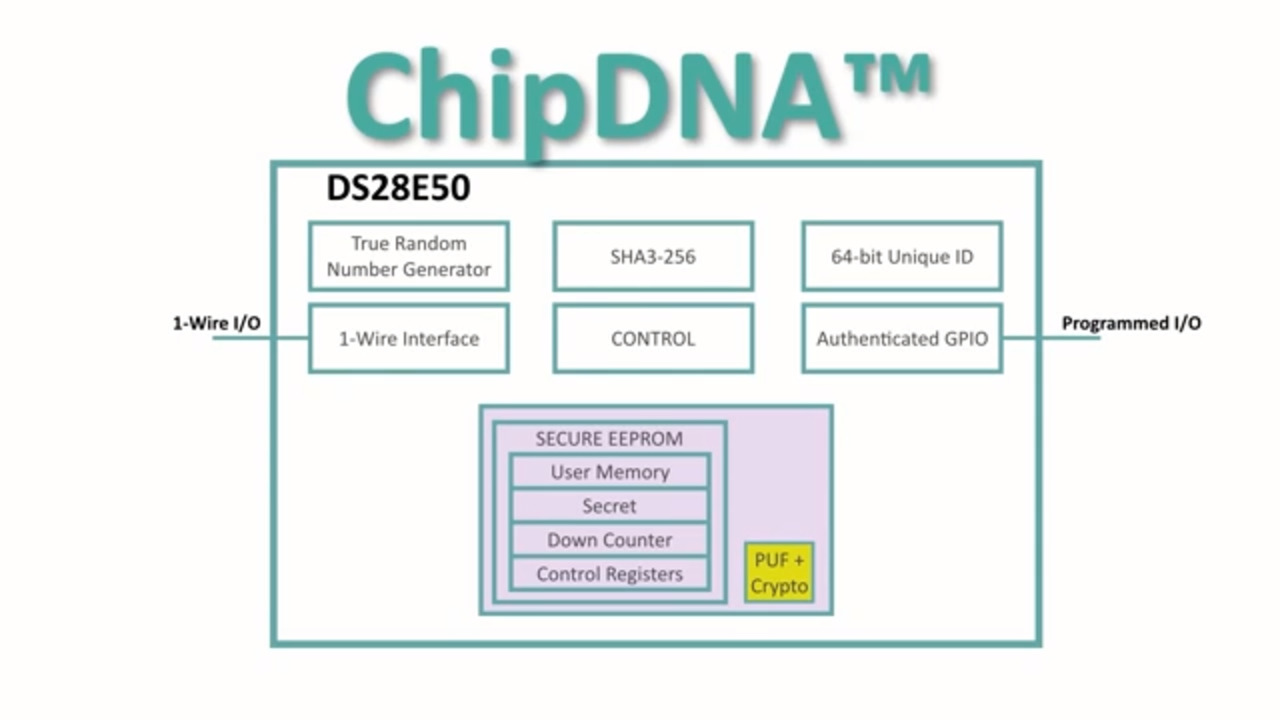
One of the more direct solutions omits key provisioning entirely. Devices like Maxim Integrated’s DS28E38 in the company’s DeepCover family are built with Maxim Integrated’s ChipDNA technology based on physically unclonable function (PUF) hardware. Such PUF-capable devices self-generate a unique identity used to create private keys that are inaccessible from external device pins.
Development systems like Microchip Technology’s Zero Touch Secure Provisioning Kit (AT88CKECC-AWS-XSTK-B-ND) include Microchip’s ECC508 authentication chip, pre-configured for provisioning with the credentials needed to connect an IoT device to Amazon Web Services (AWS).
But what about provisioning private keys and trusted microcontroller (MCU) firmware in custom designs unable to use PUF-based, self-generated identities?
Secure provisioning
In some cases, developers can use MCU manufacturers’ development environments to generate and provision these assets on supported MCUs. For example, NXP Semiconductors’ MCUXpresso Secure Provisioning Tool lets developers access the company’s open-source secure provisioning software development kit (SDK) through a graphic interface or command-line scripts (Figure 1).
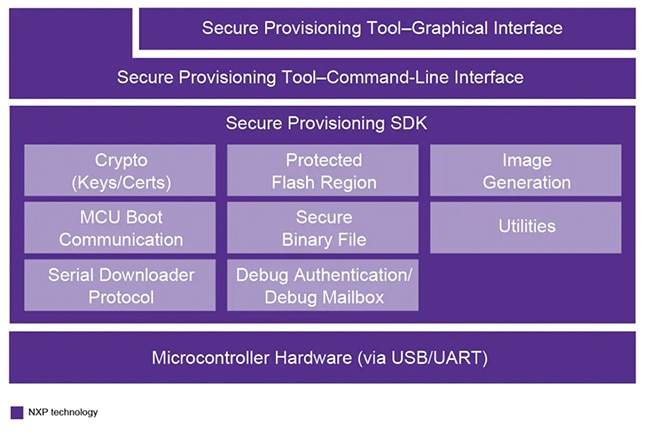 Figure 1: NXP Semiconductors’ MCUXpresso Secure Provisioning Tool offers interfaces to its open-source secure provisioning SDK. (Image source: NXP Semiconductors)
Figure 1: NXP Semiconductors’ MCUXpresso Secure Provisioning Tool offers interfaces to its open-source secure provisioning SDK. (Image source: NXP Semiconductors)
STMicroelectronics offers a solution designed to help developers protect code and data in designs built with the company’s STM32 processors when using third-party contract manufacturers. Here, developers generate an encrypted image with the STM32 Trusted Package Creator software tool and store a secret key in STMicroelectronics’ STM32HSM HSM smartcard. On receiving the encrypted image and HSM smartcard, the contract manufacturer uses the STM32 Cube Programmer to securely provision keys and firmware onto STM32 devices like x and y that support SFI (Figure 2).
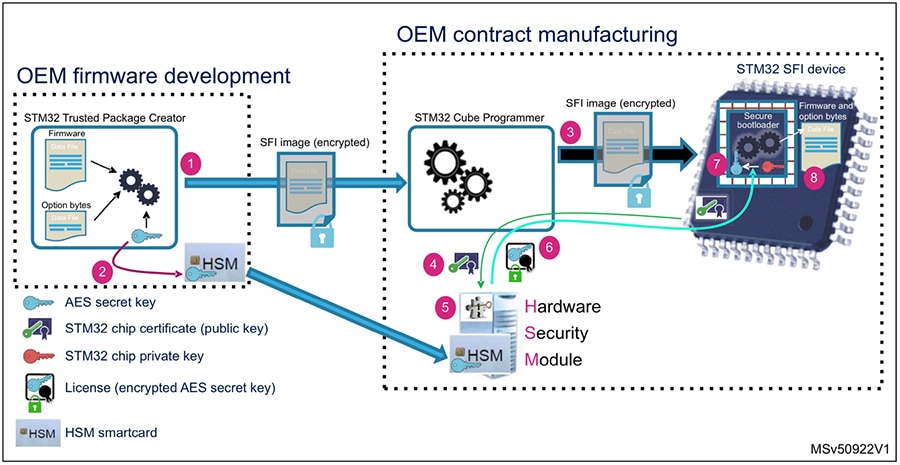 Figure 2: Developers can use STMicroelectronics’s STM32 Trusted Package Creator software and an STM32HSM HSM smartcard to safely transfer secure assets to third-party manufacturers. (Image source: STMicroelectronics)
Figure 2: Developers can use STMicroelectronics’s STM32 Trusted Package Creator software and an STM32HSM HSM smartcard to safely transfer secure assets to third-party manufacturers. (Image source: STMicroelectronics)
For developing with other devices, IAR Systems offers its Secure Desktop Provisioner integrated with its IAR Embedded Workbench. Developed with its Secure Thingz business unit, Secure Desktop Provisioner is part of a development flow stretching from secure development through prototyping, production, and later updates (Figure 3).
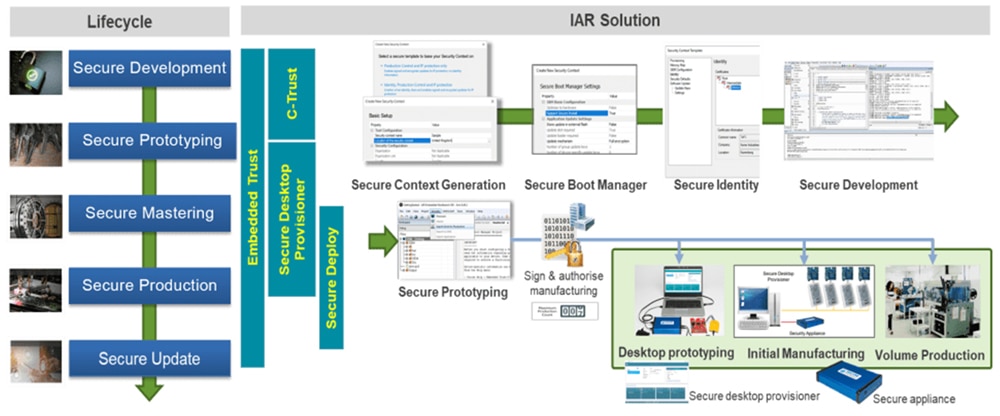 Figure 3: IAR Systems’ development flow allows designs to provision development keys and firmware to prototypes and then safely transfer assets to manufacturing where development keys are replaced with production keys. (Image source: Renesas)
Figure 3: IAR Systems’ development flow allows designs to provision development keys and firmware to prototypes and then safely transfer assets to manufacturing where development keys are replaced with production keys. (Image source: Renesas)
Working in the IAR Embedded Workbench, developers use the Secure Desktop Provisioner software tool to provision keys and firmware during preliminary prototyping stages. When the design is ready for initial manufacturing and volume production, firmware assets are transferred to manufacturing partners and development keys are replaced with secure production keys that are provisioned using a secure appliance.
Conclusion
To implement secure connected systems like IoT devices, developers not only need to take advantage of specialized security chips and processors but also need to protect the underlying secret keys and trusted firmware. Fortunately, a variety of solutions exist to protect these assets during the crucial provisioning phase of production.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum