Cloud Providers are Coming Down to the Hardware Level for End-to-End IoT Security
When I started using cloud services well over a decade ago, co-located dedicated servers were the platform of choice, and IT managers thought this cloud thing just might be useful one day for storing backups needed for disaster recovery.
On the Amazon home page, Amazon Web Services (AWS) itself was a link buried well below the "fold" (or "first view," depending on how trendy you were) and linking to an impressively dull AWS home page that could actually hold a full month of detailed AWS "What's New" announcements back then (Figure 1).
Amazon Simple Queue Service (SQS) – a core AWS service for creating loosely coupled distributed systems – had just moved from beta to general availability and AWS' flagship cloud-computing service, called Amazon Elastic Compute Service (known today simply as EC2), was in limited beta. Oh, how far we've come. But as interesting as that evolution has been, that's nothing compared to the next stage of cloud platform services that are evolving to meet the IoT's myriad requirements.
 Figure 1: Despite rapid evolution from their earliest days, cloud service offerings are moving into a new stage that promises tight integration with IoT devices. (Image source: The Internet Archive aka Wayback Machine)
Figure 1: Despite rapid evolution from their earliest days, cloud service offerings are moving into a new stage that promises tight integration with IoT devices. (Image source: The Internet Archive aka Wayback Machine)
There's a sort of fundamental impedance mismatch between resource-constrained IoT end nodes built by embedded systems developers and cloud applications running on virtualized resources built by hardcore infrastructure specialists. On the face of it, it seems so simple: You just add the appropriate communication stacks and interact through their associated APIs. How hard can it possibly be to use a few REST calls at the bare minimum to push sensor data to some cloud-based endpoint? That's rarely the problem. It's so easy to build connected systems that you can find any number of seemingly straightforward designs for connected "smart" products.
If that's all you do though, you're likely to become the next meme on social media because that mismatch between IoT devices and cloud services has until recently shown itself most strongly where it's most damaging – in end-to-end security.
Security that extends throughout the IoT application hierarchy from IoT end nodes to cloud-based enterprise resources is difficult to achieve, but often not for the reasons that first come to mind. For the IoT, security has become so strongly tied conceptually to its underlying mechanisms such as encryption protocols and authentication that it's easy to lose track of the overall application: The forest is well hidden by the trees.
In fact, we have access to so many security devices that can lock down communications, lock out unauthorized users, and mitigate an increasing number of threats. Manufacturers are routinely integrating crypto accelerators in MCUs targeting vulnerable application areas such as the IoT, and specialized security chips designed to minimize threat surfaces. Even so, the most careful application of low-level security mechanisms can still result in spectacular security failures if designs and applications are created with limited attention to the overall security application framework for the entire IoT application hierarchy.
The good news is that cloud providers are reaching more deeply than ever into hardware in ways that should help eliminate this frustrating mismatch between cloud security services and devices. For example, Microsoft's recently announced Azure Sphere promises to tighten device-to-cloud security with devices that integrate Microsoft's Pluton security subsystem in multicore designs from familiar Arm®-based semiconductor manufacturers including Nordic Semiconductor, NXP Semiconductors, Silicon Labs, and STMicroelectronics.
You don't need to wait for the next stage of the IoT cloud evolution to begin leveraging its benefits. AWS has collaborated with Microchip to enable "zero-touch" secure deployment using the Microchip Technology ATECC508A security device. For secure systems operations, AWS offers a tight integration for IoT systems through its Amazon FreeRTOS real-time operating system certified on multiple hardware platforms including:
- Microchip Curiosity PIC32MZ EF development board
- NXP LPC54018 IoT Module
- STMicroelectronics STM32L4 Discovery Kit IoT Node
- Texas Instruments CC3220SF-LaunchXL
Running on these platforms, Amazon FreeRTOS and associated AWS services will let you more easily achieve secure connections and support secure firmware updates critical to IoT lifecycle operations for IoT end nodes and edge devices (Figure 2).
 Figure 2: Amazon Web Services (AWS) extends deeply into IoT device platforms with its Amazon FreeRTOS designed to simplify secure connections and firmware updates. (Image source: Amazon Web Services)
Figure 2: Amazon Web Services (AWS) extends deeply into IoT device platforms with its Amazon FreeRTOS designed to simplify secure connections and firmware updates. (Image source: Amazon Web Services)
Google has also described a sophisticated IoT connectivity approach that combines the Microchip ATECC608A security device with a novel approach able to support mutual authentication without the usual overhead of conventional TLS-based authentication (Figure 3).
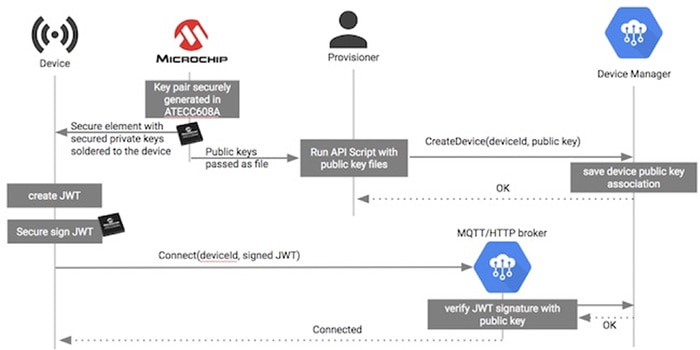 Figure 3: Google leverages the Microchip ATECC608A security IC and a JSON Web Token (JWT) to provide mutual authentication between an IoT device and its Device Manager cloud service without the overhead associated with conventional TLS authentication. (Image source: Google)
Figure 3: Google leverages the Microchip ATECC608A security IC and a JSON Web Token (JWT) to provide mutual authentication between an IoT device and its Device Manager cloud service without the overhead associated with conventional TLS authentication. (Image source: Google)
These specific options just scratch the surface of the types of integrated offerings available that are rapidly emerging from increased collaboration between semiconductor manufacturers and cloud service providers. By combining these solutions within a broader security policy, you'll stand a good change of keeping your products out of the worst kind of headlines.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum