Workload Consolidation is a Good Thing, Right?
Workload consolidation is a great idea: do more with less to lower cost and increase functionality. Two of the primary drivers for workload consolidation are artificial intelligence (AI) and machine learning (ML). AI and ML can both be implemented in the cloud, but for many applications, cloud latency makes this less than feasible. The fix is to bring AI and ML out to the edge.
As you might expect, that action brings about its own set of issues that must be considered. Workload Consolidation and Security for AI and ML explores how security changes with workload consolidation. With advances in new processors and higher levels of integration, there’s certainly more processing resources available at the edge than ever before. For example, the S32V2 series from NXP makes it possible to implement new levels of real-time vision and neural network processing in a wide range of applications.
One important aspect that must be considered is that when you bring processing out to the edge, you bring your IP out with it. No one wants to steal the interpolation algorithm in your temperature sensor. But AI and ML are emerging industries. This technology is still nascent, and frankly, it’s hard. There’s still lots of room for innovation, and companies are differentiating their products from their competition with how they process data and implement their proprietary complex algorithms. As these technologies advance, at some point they will become available as off-the-shelf libraries, much the same way graphics libraries, digital signal processing, speech recognition, and any of a thousand technologies have gone.
But we aren’t there yet, and when your IP is out at the edge, it’s vulnerable. It can be stolen by your competitors if you don’t protect it. So the more valuable the IP you bring to the edge, the more important it is to protect it. You can’t just store it in flash memory because it isn’t that hard to read your code off the memory bus. Code has to be encrypted, and your cryptographic keys need to be stored in a way that they can’t be read off the microprocessor.
But even this isn’t enough. There’s still the vulnerability of the processor itself. If a hacker can upload new code, either as an update or over a debug port, a simple program overwriting your firmware can use the processor’s cryptographic engine to decrypt your code and feed it out through an I2C port.
To protect IP, the processor itself must be secure. This starts with technology like secure boot. Consider the Sitara series of processors from Texas Instruments (Figure 1). These embedded processors establish a trusted root by verifying the integrity of boot firmware before the processor begins any code execution. Once established, the application can be securely loaded and executed, building from this root of trust.
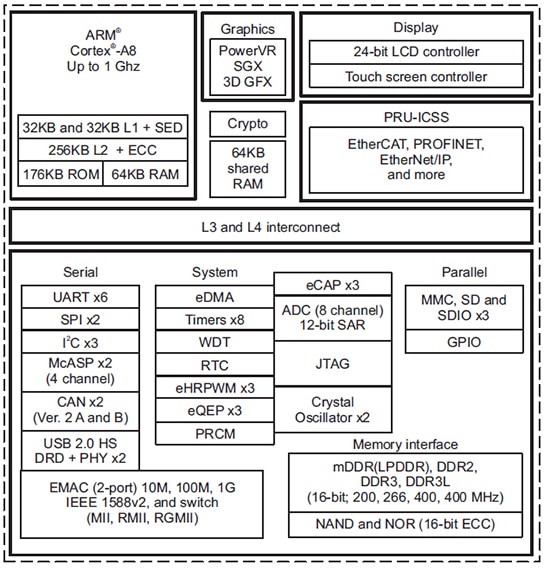 Figure 1: Functional block diagram of Texas Instruments’ Sitara AM335x microprocessors. (Image source: Texas Instruments)
Figure 1: Functional block diagram of Texas Instruments’ Sitara AM335x microprocessors. (Image source: Texas Instruments)
Workload consolidation at the edge enables systems to do more work locally and achieve greater functionality through real-time access to data. At the same time, systems also need to have more security to protect the IP that would now otherwise be exposed. With today’s embedded processors and their integrated security capabilities, IP can be secured. So yes, workload consolidation is a good thing.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum