Workload Consolidation and Security Maximizes AI and ML
Contributed By DigiKey's North American Editors
2020-01-27
The increased connectivity enabled by the Internet of Things (IoT) lets developers consolidate workloads either locally or in the Cloud. This enables a wide range of complex systems to do more with less and bring advanced capabilities like artificial intelligence (AI) and machine learning (ML) out to the edge.
Many embedded, industrial, automotive, and medical applications can benefit from AI and ML. For example, industrial systems can employ vision processing, neural networks, and other types of complex algorithms to improve production and efficiency. To do so, these systems must be able to process large amounts of data in real-time.
Certain applications have the luxury of being able to connect to the cloud to access massive processing resources. For example, industrial systems can send performance data to the cloud for later processing to assess whether machinery is operating as expected. As anomalies in data are detected, action can be taken to correct operation—either manually or through adjustment of operational algorithms—to improve performance and defer future maintenance.
Many applications, however, can’t tolerate the latency of cloud access. Autonomous vehicles, for example, need to process video quickly to make real-time driving decisions that can impact driver safety. Similarly, industrial systems employing vision processing need to act on that data in a manner that doesn’t materially slow the manufacturing line.
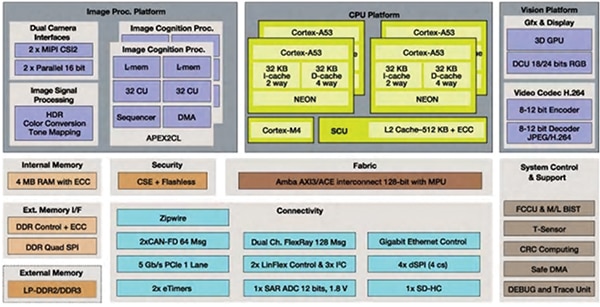 Figure 1: Processors like the NXP S32V234 enable new levels of both real-time vision and neural network processing in a wide range of applications by combining multiple processors on the same chip. The S32V234 combines an image signal processor (ISP) with a 3D graphics processor unit (GPU) and dual APEX-2 vision accelerators. (Image source: NXP)
Figure 1: Processors like the NXP S32V234 enable new levels of both real-time vision and neural network processing in a wide range of applications by combining multiple processors on the same chip. The S32V234 combines an image signal processor (ISP) with a 3D graphics processor unit (GPU) and dual APEX-2 vision accelerators. (Image source: NXP)
Processors such as the S32V2 series from NXP enable new levels of both real-time vision and neural network processing in a wide range of applications. The S32V234, for example, combines an image signal processor (ISP) with a 3D graphics processor unit (GPU), and dual APEX-2 vision accelerators (see Figure 1). The MPU delivers automotive-grade reliability and important functional safety capabilities required for advanced driver assistance systems (ADAS). It also integrates hardware-based security and encryption capabilities to ensure data integrity and protect systems against hackers.
Security at the Edge
There are some disadvantages to consolidating processing resources locally and bringing AI and ML functionality out to the edge. Security is chief among them. Three ways that developers need to consider security in intelligent edge applications include protecting integrity, privacy, and IP.
Protect Integrity: Modifying system code is not the only way to hijack a system. For example, intelligent systems make decisions based on real-time data. If the data behind these decisions can be modified, the system can be controlled. Consider an industrial motor implementing predictive maintenance. When data shows that the motor is under stress, an algorithm can adjust operation to relieve the motor and extend its working life. The opposite is possible as well. A hacker who can modify incoming motor data can trick an algorithm into adjusting operation to cause the motor to adversely stress itself, resulting in system failure or damage. Imagine if that machine is a medical device that’s hacked to diagnose patients as healthy when they aren’t. Similarly, systems are also at risk from users. For example, a person or company might be willing to hack their utility meter to “reduce” their consumption and pay a lower bill.
Protect Privacy: While the need to protect user privacy may be a controversial issue, laws such as Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) make not managing privacy an increasingly expensive oversight. Consider any IoT application that collects data about a user, especially medical equipment. If user information can be compromised, this puts a company at risk to potentially massive penalties.
Protect IP: With the availability of real-time data and low-cost processing resources at the edge, there’s tremendous opportunity for companies to add value to their products through AI and ML. Given that this is where much of a company’s development efforts will be focused, more of a company’s important assets will be in its intellectual property (IP).
This IP is what differentiates many companies from their competition, especially the “me too” copycats that enter markets that have recently been opened through innovation. If this IP is readily accessible, such as being able to be copied out of a processor’s memory, OEMs can find their IP investment profiting other companies. To prevent this, OEMs need a robust way to secure their firmware and application code from being copied.
To address these risks, systems need to implement security to protect data integrity and privacy, and system IP. This means that IoT-based systems need to protect data and code not only when it passes over the Internet, but also internally within the processor where it resides.
Such security needs to be implemented in hardware. This means not just encryption algorithms, but also the mechanisms that prevent data and code from being exposed in the first place. Consider code stored in external flash memory and then loaded into a processor. The code must be encrypted in the flash to be protected, otherwise a hacker could read the code off the memory bus when it’s loaded into the processor. In addition, the processor firmware must be secure. If firmware is not secure, then a hacker could load rogue code into the processor, which could then read and decrypt the code stored in flash.
 Figure 2: The Sitara series of processors from Texas Instruments is a powerful portfolio of processors supporting the range of security features necessary to build secure systems. (Image source: Texas Instruments)
Figure 2: The Sitara series of processors from Texas Instruments is a powerful portfolio of processors supporting the range of security features necessary to build secure systems. (Image source: Texas Instruments)
The Sitara series of processors from Texas Instruments are an excellent example of a powerful embedded processor that supports the security features necessary to build secure systems (see Figure 2). With the AM335x, AM4x, AM5x, and AM6x families, developers can build robust Industry 4.0 applications with increased performance and connectivity.
Sitara security employs secure boot, the foundation of a secure processor. Secure boot establishes a root of trust for the system by verifying the integrity of the boot firmware. From this known and trusted root, the rest of the system can be brought up in a secure manner using standard encryption technology, including AES and 3DES encryption. In addition, code can be stored encrypted in an external flash, thus securing the integrity of the code and protecting IP from being stolen. With a secure code base, OEMs can ensure both the integrity and privacy of data within the system.
Consolidating workloads at the edge enables systems to implement artificial intelligence and machine learning to increase the productivity and efficiency of systems across all applications. Today’s integrated processors, like the S32V2, deliver powerful capabilities in a single chip, enabling wholly new applications. In addition, OEMs can innovate new features that rely upon access to real-time data.
As data processing moves to the edge, however, security concerns increase. To ensure data integrity, data privacy, and IP protection, processors need to integrate advanced security features. Embedded processors like the Sitara series integrate security capabilities such as secure boot and hardware-based decryption to enable OEMs to create truly secure systems. In this way, OEMs can minimize security risks and reduce potential losses for end users.

Disclaimer: The opinions, beliefs, and viewpoints expressed by the various authors and/or forum participants on this website do not necessarily reflect the opinions, beliefs, and viewpoints of DigiKey or official policies of DigiKey.