State-Backed Cyberattacks Focus on Supply Chain
In an increasingly global economy, the importance of cyber security in the supply chain is hard to overstate. State-backed bad actors have many opportunities to cause significant disruptions and data compromises. Those involved in the electronics supply chain, particularly semiconductors, must be vigilant in managing these threats.
Cybercrime rising
As business transactions go increasingly virtual, cyberattacks are on the rise. Resilinc’s EventWatch, which monitors and tracks supply chain cyberattacks, saw 738 attacks in the first eleven months of 2024. In the first half of 2024, attacks increased 21% compared to the first half of 2023. Over the five years from early 2019 to early 2024, cyberattack alerts increased by 1,375%.[1] The rise in attacks can be traced to the gap caused by shortages of IT workers and the increase in online activity.
A subset of overall cyberattacks are launched or supported by governments to advance their political, economic, or military interests. These attacks often target other governments, critical infrastructure, large corporations, or key industries. According to Crowdstrike, technology is the most frequently targeted industry vertical of the top ten, and North America is by far the most popular target geographically (Figure 1).
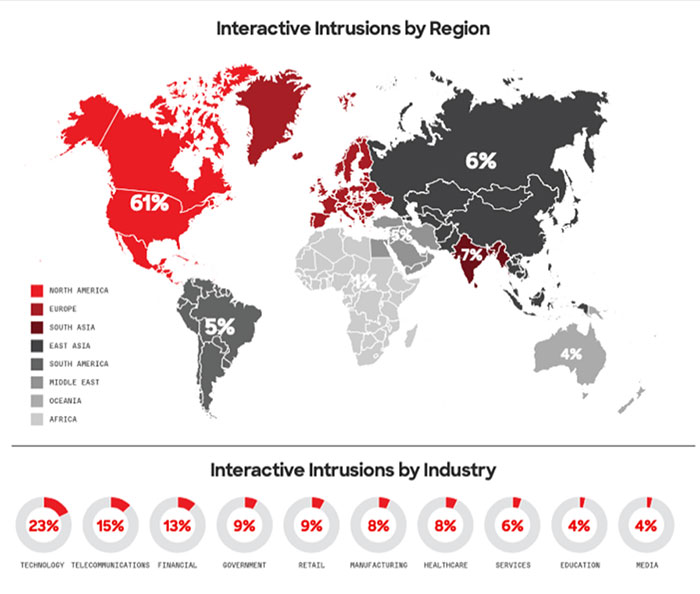 Figure 1: Technology is the most frequently targeted industry vertical of the top ten, and North America is the most popular target geographically. (Image source: Crowdstrike)
Figure 1: Technology is the most frequently targeted industry vertical of the top ten, and North America is the most popular target geographically. (Image source: Crowdstrike)
State actors, comprising individuals or groups that act on behalf of or with the support of a government or nation state, step onto this battlefield without the goal of financial gain. Instead, these attackers seek to gather sensitive information, disrupt critical infrastructure, or sway public opinion. In the global supply chain, this translates into malicious actions aimed at organizations producing and distributing goods. Nearly every country has the potential to involve itself in nation-sponsored cybersecurity attacks.
Software & hardware
State actors have two different vectors of attack on the technology supply chain. First, by exploiting third-party vendors and service providers upstream, attackers can infiltrate systems when users install software across a wide variety of potential targets (Figure 2). Second, software developers frequently turn to open-source code for efficiency and innovation, and to get to market quickly. By infiltrating these shared resources, bad actors can gain a foothold and create widespread disruption.
 Figure 2: Threat actors multiply their attack vectors by moving upstream to infiltrate third-party software applications. (Image source: Darktrace)
Figure 2: Threat actors multiply their attack vectors by moving upstream to infiltrate third-party software applications. (Image source: Darktrace)
State actors are increasingly employing these approaches. According to Gartner, software supply chain attacks, including proprietary and commercial code, pose significant security, regulatory, and operational risks to organizations.3 The research firm estimates that costs associated with these attacks will rise from $46 billion in 2023 to $138 billion by 2031.
Hardware provides another attack vector for nation-state threat actors. By tampering with device hardware and firmware, bad actors can target end customers' data, and the supply chain is the potential weak link for introducing malware. According to a recent study by HP, almost one in five (19%) organizations have been impacted by nation-state threat actors targeting PC, laptop, or printer supply chains.4 In the United States, this figure is significantly higher at 29%.
What to do
Clearly, cybersecurity in the supply chain should be a high priority for OEMs. As the complexity and sophistication of attacks increase, the industry will have to work together to address the threats. Individually, OEMs need to use various tools, including encrypting data, enforcing strong access controls, regular software updates, employee training, and continuous monitoring to mitigate escalating threat levels.
At the industry level, the SEMI Cybersecurity consortium was launched earlier this year. Its mission is to develop and promote a standards-based, industry-wide approach to improve cybersecurity and accelerate the implementation of actionable solutions. The consortium has pledged to focus on three key actions over the next year:5
- Developing a robust framework for cybersecurity that incorporates lessons learned from the recent transition and embraces open collaboration.
- Creating a semiconductor industry-specific framework to assess the strength of cybersecurity across the supply chain and implement measures to better protect ecosystem networks.
- Incorporating best practices from industries such as automotive and medical to modernize security protocols and facilitate collaborative information sharing through SEMI.
Nation-state threats are rising, and attack vectors are becoming more prolific in the electronics supply chain. Meanwhile, cyberattackers are becoming increasingly sophisticated. A combination of good cybersecurity practices and increasing industry collaboration will help mitigate their impact.
References
2: https://go.crowdstrike.com/global-threat-report-2024.html
3: https://www.gartner.com/en/documents/5524495
4: https://www.hp.com/us-en/newsroom/press-releases/2024/hp-wolf-security-study-supply-chains.html

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum