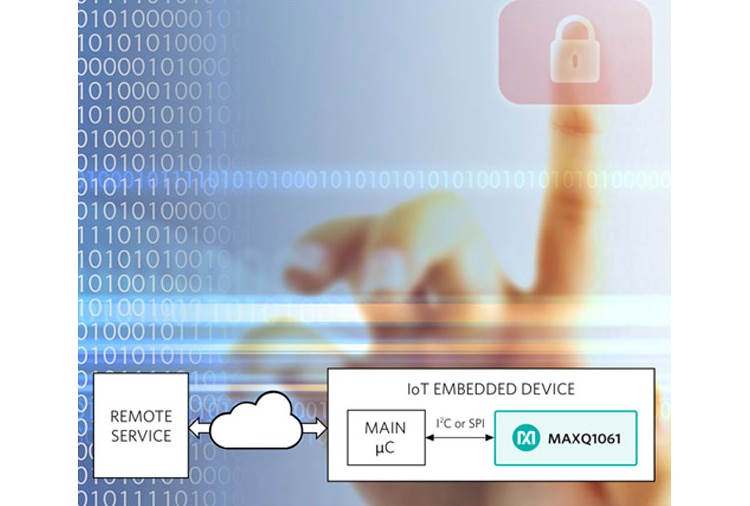
Software vs. Hardware Hacking
Encryption, whether hardware or software, minimizes security breaches and adds layers of protection to secure data. There are typical differences, however, as to when hardware and software encryption is used, and why.
Software encryption typically protects an organization’s devices, given its cost effectiveness, and ease to upgrade/update. Able to protect data at rest, stored, and in transit, this encryption is often supported by features that bolster and complement encryption.
In comparison, hardware-based encryption exists on a device’s on-board security, performing encryption and decryption, without additional software, and making it free from contamination, malicious code infection, or vulnerability. Used most often to protect sensitive data on portable devices, it also protects data at rest. Drives with sensitive data are best protected through hardware keys that protect the data even if the drives are stolen. Hardware solutions are more expensive and require upgrades to the hardware platform versus just doing software upgrades/updates—a much more inexpensive option.
Software vulnerabilities
It must be pointed out that still, even two decades into this century, there are companies that choose to not adequately secure their data. This includes not updating, upgrading, or changing passwords, failing to employ multiple protection methods, and often, not even changing the resident password codes on devices they plug into their network. This creation of low-hanging fruit for the hacker represents a large percentage of security vulnerabilities that are easily avoidable.
Other vulnerabilities include (but are not limited to):
- The lack of strong encryption on stored data
- Stuffing too much data into too-small memory, especially in mobile apps written in C/C++, which is particularly vulnerable to buffer overflows
- Access to data directly via unsecure services and APIs
- Not controlling access to log files, enabling hackers to trace security vulnerabilities
- Code reuse that can bring parasitic code from other sources into the enterprise
- Hackers using path traversal, creating a dot-dot-slash attack
- Cross-site scripting whereby attackers execute code in your website visitors’ browsers
- Insufficient authentication beyond log in
Hardware vulnerabilities
Hardware vulnerabilities most often depend on how well the circuit is designed to protect private keys from attack. The reason attacks get through include (but again, are not limited to):
- Interception of electromagnetic waves in an electromagnetic side-channel attack
- Not using an MCU with a secure debug feature
- Not creating anti-tampering techniques that indicate a tamper condition and wiping a private key from memory if tampering occurs
- Not ensuring a secure boot
Potential solutions
There are a variety of security-based solutions on the market and the number grows constantly. Here are a few suggestions to consider. Use a hardware-based security core. The Silicon Labs Wireless Gecko Series 2, for example, features an integrated security core. Watch a First Look Video on this recently announced technology.
Consider the Microchip CryptoAuthentication SOIC XPro starter kit featuring a SAMD21-XPRO and an AT88CKSCKTSOIC-XPRO socket board and Crypto Authentication sample devices. Used with Microchip's Crypto Evaluation Studio (ACES), the kit supports all Crypto Authentication devices including the ATECC608A, ATECC508A, ATECC108A, ATSHA204A, and ATAES132A.
The AWS Zero Touch Secure Provisioning Kit, also by Microchip, features a complete development and prototyping platform for AWS IoT device provisioning. As shown in Figure 1, it includes three customized (ATCRYPTOAUTH-XAWS) add-on boards, each containing an AWS configured ECC508 for in-situ provisioning by the kit signer script. Also included are Secure Root and Signer Provisioning Scripts. The kit is built on the modular Xplained PRO platform, and it enables experimentation with different processors, connectivity, and human interactivity interface modules.
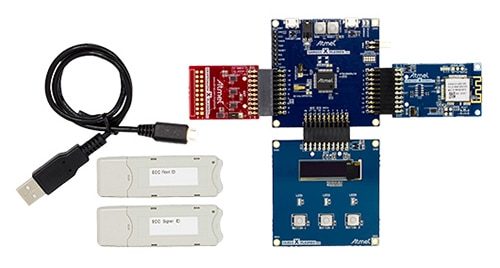 Figure 1: The Microchip AWS Zero Touch Secure Provisioning kit enables the fast and easy design of IoT devices that comply with new AWS security regulations. (Image source: Microchip)
Figure 1: The Microchip AWS Zero Touch Secure Provisioning kit enables the fast and easy design of IoT devices that comply with new AWS security regulations. (Image source: Microchip)
The NXP OM-SE050ARD development kit allows for the evaluation of the SE050 product family features and simplifies secure IoT application development (Figure 2). The secure EdgeLock element for IoT devices provides a root of trust at the IC level and delivers real end-to-end security, from edge to cloud, without the need to write security code.
 Figure 2: The NXP OM-SE050ARD represents a flexible and easy development kit for the EdgeLock SE050 family of products. (Image source: NXP)
Figure 2: The NXP OM-SE050ARD represents a flexible and easy development kit for the EdgeLock SE050 family of products. (Image source: NXP)
Another kit to help you secure your design is Infineon Technologies’ Blockchain Security 2Go starter kit, delivering a fast and easy way to build in best-in-class security. The kit includes ready-to-use NFC cards for secure key generation; signing methods, and pin protection; on-card software supporting commands for key-management; and signature creation and PIN authentication and access to Infineon’s blockchain hub. One potential Blockchain application is identity management, used as the foundation of an authentication system.
Attacks are now too common and are becoming more sophisticated. Start protecting on both the software and hardware fronts and don’t be that low-hanging fruit that gets hit first and fast. Then, consider where you’re most vulnerable and review the options that are increasingly available.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum