A Tale of Two Hardware Security Solutions for IoT Designs
Security has been a second-class citizen in embedded designs, mainly due to time and cost factors. There have been other factors too, such as embedded security becoming synonymous with complexity. The lack of appreciation for the importance of security and how to efficiently implement it have also played a role.
The outcome: security became a design afterthought with engineers placing software patches here and there. But that’s changing, thanks to hyper-connected embedded Internet of Things (IoT) nodes. These mandate highly secure designs to counter vulnerabilities in connected thermostats, refrigerators, CCTV, and HVAC systems.
Here, at this technology crossroads, it’s worth noting that the IoT is a highly diverse design world and there is no one-size-fits-all security solution. Even in the security threats fold, you have physical vulnerabilities such as tampering attempts, design cloning, IP theft, and product counterfeiting. On the cyber-attack frontier, there are malware injections, distributed denial-of-service (DDoS) attacks, and side-channel attacks.
However, unlike server and gateway designs which can afford extensive security investments, IoT nodes such as connected thermostats demand a simpler security mechanism that can counter both physical and communication vulnerabilities while meeting the cost and power usage constraints.
In order to provide cost-effective protection against physical and remote attacks, Microchip Technology’s SAM L11 microcontrollers offer a simple security implementation for low-power IoT nodes. The processor is clocked at 32 MHz and is supported by a memory configuration of up to 64 Kbytes of flash and 16 Kbytes of SRAM. On-board picoPower technology ensures low energy usage in both active and sleep modes.
For key provisioning, the SAM L11 allows you to use third-party services from software houses like Trustonic, Secure Thingz, and Segger Microcontroller Systems. This greatly simplifies things by abstracting the lower-level details of the MCU’s security features with a modular GUI interface.
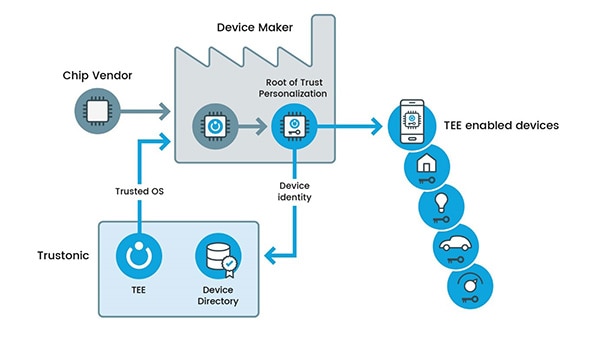 Figure 1: Trustonic’s key provisioning service abstracts lower level details of SAM L11’s security functions. (Image source: Trustonic Inc.)
Figure 1: Trustonic’s key provisioning service abstracts lower level details of SAM L11’s security functions. (Image source: Trustonic Inc.)
You can simply pick and choose security features relevant to the application. However, SAM L11 also lets you develop your own provisioning software and implement it using the code examples and product demos.
Next, SAM L11 combines chip-level security with Arm’s TrustZone for Armv8-M to isolate secure firmware from software code that is not safety critical. The TrustZone environment, for example, can protect the communication protocol stack in a thermostat from malicious attacks that can allow hackers to take control of a smart home.
Secure element vs. hardware security module (HSM) solutions
What if you are looking for a more robust security framework for your IoT design? The one that can spot a weak link in the entire IoT application ecosystem?
Here, it’s worth mentioning that hardware-based security in embedded systems is generally synonymous with chips incorporating a hardware security module (HSM), which acts as an independent security guard to monitor the data exchange. It’s effectively an isolated subsystem within a chip that runs advanced security algorithms to ensure protection against malicious attacks.
But while HSM-based approaches offload the main CPU from security-related tasks, it can be a costly and cumbersome arrangement that mandates a sophisticated database for the storage and distribution of security keys.
For sure, large companies with volume production can better afford the HSM-based security solutions. But what about smaller volume IoT designs that also demand a robust security solution against hackers and spoofs targeting digital assets in MCUs? This is where secure element comes in.
Secure element is an expensive microcontroller that communicates with the main MCU or MPU over I2C or single-wire interface. It protects the connected devices by carrying out end-to-end authentication.
For example, a security element like Microchip’s ATECC608A performs three fundamental tasks: security key generation, crypto acceleration to perform mutual authentication, and key storage in a secure memory space. In other words, it creates secure boundaries for private keys and isolates them from other software components. That, in turn, prohibits hackers from getting hold of the supply and clock signals in an IoT device design and using that information to create a backdoor channel for launching side-channel attacks.
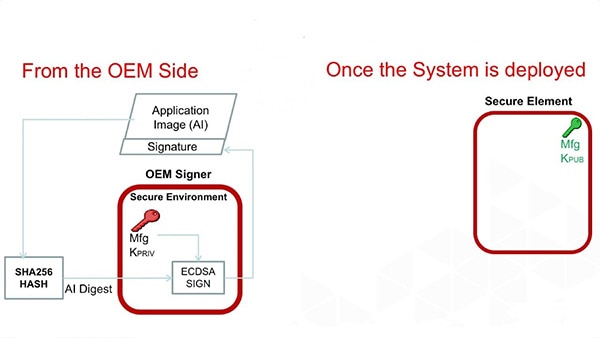 Figure 2: A view of Microchip’s ATECC608A secure element implementing the key provisioning in an IoT device. (Image source: Microchip Technology)
Figure 2: A view of Microchip’s ATECC608A secure element implementing the key provisioning in an IoT device. (Image source: Microchip Technology)
Secure elements are gaining traction in IoT designs. Cloud service providers like Google and Amazon Web Services (AWS) are endorsing the ATECC608A for linking IoT nodes to the cloud. And TrustZone technology complements the ATECC608A by providing firmware protection within an IoT design framework. Those are pretty big endorsements!
The secure element chip also comes with an upgraded random number generator (RNG) to comply with the new National Institute of Standards and Technology (NIST) requirements defined in the SP800-90A/B/C bit generation standards.
Conclusion
The connectivity-centric vulnerabilities in IoT designs have thrust security issues to the forefront. Though the number of connected devices is still higher than security design implementations, the availability of low-cost security chips with a focus on simplifying the key provisioning could soon shift the balance.
What’s also apparent is that hardware and software solutions are coming together to jointly protect IoT devices against an ever-increasing number of attack vectors. This alliance between the hardware and software worlds could also help overcome the steep learning curve required to implement robust security solutions.

Have questions or comments? Continue the conversation on TechForum, DigiKey's online community and technical resource.
Visit TechForum