Providing Peace of Mind in the Wireless IIoT World
Contributed By DigiKey's European Editors
2017-08-24
Wireless communications offer significant advantages in the world of industrial control and automation. The number of wireless devices in any automated industrial operation has significantly increased, all connected to form an Industrial Internet of Things (IIoT) consisting of equipment, routers and sensors. Moreover, all have specific communications needs and requirements.
Operating a process within such a comprehensive control environment is quite involved and can pose a great challenge. Consider multiple sources of data requiring different protocols and data types. Data, voice, video and control signals—an IIoT network must have the bandwidth and the network management intelligence to avoid data loss due to simple signal drop-out or malicious intent. In these situations, data loss is productivity loss.
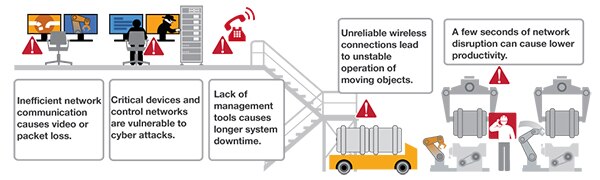
Figure 1: IIoT overview.
In the world of IIoT, devices must be robust enough to handle the industrial environment. The industrial landscape can vary from a sterile medical facility to the dark depths of a uranium mine. Solutions must be flexible and reliable. Devices must also tolerate temperature variations, shock, vibration and the specific hazards of the workplace, and must meet Federal and local codes and standards. Perhaps most importantly, the system must be secure and safe. Data disruption due to network hacking or malicious software is an important issue when it comes to wireless IIoT operation. An insecure system serves as a danger to the operating systems/devices and human workers.
The drive toward industrial automation is all about process efficiency and maximizing productivity. IIoT is all about collecting data, analyzing trends, making informed decisions through connected devices, and ultimately maximizing productivity. The advantages of the IIoT are well known. Implementation requires much forethought. Smart planning and quality equipment are essential to ensure efficient and secure operation on a wireless network. When adding a device to the network, wireless communication is the desirable option due to ease of installation and cost savings.
The challenge for the embedded developer is designing a platform from which they can build a secure, reliable and trusted solution from the beginning. Developing any embedded design from scratch can be a daunting task even for the most experienced engineer, and adding security functionality and being able to thoroughly test it can take a lot of time. Helping this process greatly while speeding time to market has meant that many development teams are opting to base their designs around a pre-certified single board computer (SBC) module, an example of which is the ConnectCore 6UL family from Digi International.
Building a secure IIoT device
A good fit for any IIoT design is Digi’s extremely compact ConnectCore® 6UL system-on-module (SOM) solution. It provides a powerful, secure and cost-effective wireless system in a package about the size of a postage stamp. It is also conveniently available as an SBC, the ConnectCore® 6UL SBC Pro.
The ConnectCore® 6UL SBC Pro is a feature rich, secure, pre-certified embedded system. It is based on the NXP i.MX6UL-2, ARM® Cortex®-A7 processor and also hosts a media co-processor. This ultra-flexible design easily integrates into any IIoT project with minimal cost and design effort.
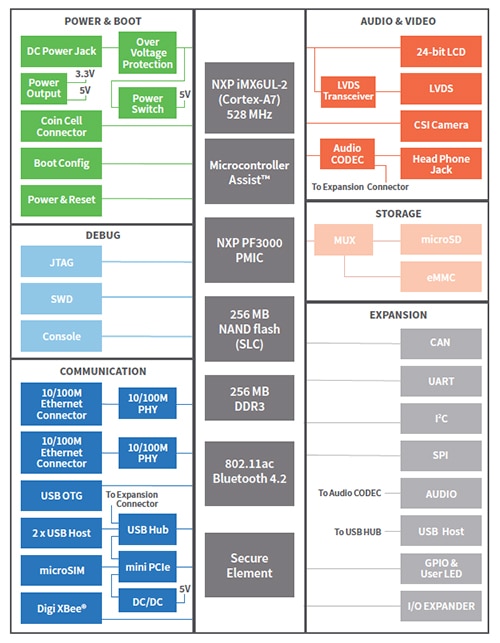
Figure 2: ConnectCore® 6UL block diagram.
Typical application environments include the medical, transportation and industrial automation sectors.
An advantage to an SBC design like the ConnectCore® 6UL is that it is pre-certified and ready to install out of the box. Dual-band 802.11a/b/g/n/ac Wi-Fi and Bluetooth 4.2, including Bluetooth Low Energy, are standard communication peripherals. Also included is the capability to add cellular connectivity with minimal effort and cost. Dual-band Wi-Fi is effective in managing and increasing throughput by providing more communication channels.
This SBC is rugged enough to handle most industrial settings. It can handle temperature ranges from -40°C to 85°C and high humidity environments, and has earned many IEC 60068 certifications which include vibration and shock immunity. With a 100 mm x 72 mm form factor, it is small enough to fit into almost any environmental control enclosure.
Embedded developers will be very familiar with the advantages of using a pre-certified SBC. What will stand out with the ConnectCore® 6UL is that it includes a complete and tested Yocto-based Linux security framework, TrustFence™, which provides engineers with the tools to design secure and reliable connected products. This approach means that core security functions can be built into any IIoT design as part of the main development process rather than having to search out and add such sophisticated security functionality once the initial application design has been created. The availability of a comprehensive ConnectCore 6UL development kit will further speed the solution design from workbench to end product.
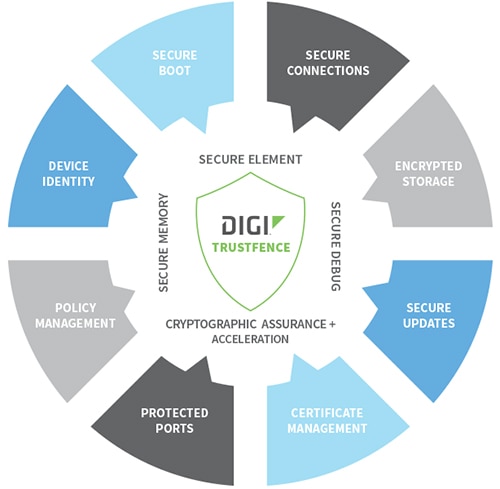
Figure 3: TrustFence™ security suite.
Digi TrustFence aids the provision of secure connections, authenticated boot, access controlled ports, encrypted data storage and secure software updates in order to protect data and device integrity, enabling engineers respond to their IIoT security mandate as well as keeping cost and development time to a minimum.
Security as an intrinsic function
Within the ConnectCore 6UL Yocto Linux, the TrustFence features are enabled through use of a class parameter within the conf/local.conf configuration file. Individual TrustFence features are also enabled in this way. For example, the secure boot function allows use of an ‘open’ device, where no checking of the boot image takes place, compared to the ‘closed’ state where only properly signed U-Boot images can be used to boot the device. A one-time programmable master key (OTPMK) is used for this purpose. In addition, secure boot can operate in a manufacturing mode where the device’s authentication and encryption keys are protected, and in the deployment mode where the boot image’s digital signature is verified prior to the image being decrypted so the device can fully boot. The most popular method of providing a digital signature is through the use of asymmetric cryptography techniques where a pair of keys (the public key and a private key) are created.
Other security functions available within the ConnectCore’s TrustFence capabilities include encrypting the partition where data is stored, a physical tamper detection interface, and securing the device’s JTAG interface – typically the first attack point an intruder might use that has physical access to the device.
Digitally signing a boot image will ensure that a device’s capabilities are never compromised through the use of an illegal firmware image. Digi’s embedded Yocto uses its stored private key (Figure 4) to encrypt the firmware image hash and sign the image. The signed image, complete with a public key and digital certificate are then written to the device’s flash memory.
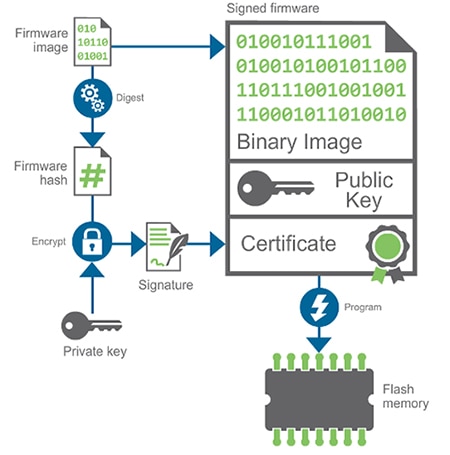
Figure 4: Digital signing of firmware image.
Booting from a signed image is a two-stage process. First, the public key used within the image is compared against the master public key held in the ConnectCore device. The boot process is aborted if they do not match. If they do match, then the boot can then process to the second stage illustrated in Figure 5.
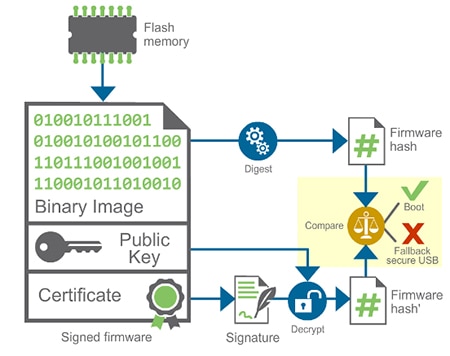
Figure 5: Boot process from a signed firmware image.
The validated public key is used to decrypt the firmware hash of the signed certificate which is compared against the hash derived from the image. If they agree, then the boot process can commence. A further step in this process can be created if necessary to encrypt the image itself. This provides a greater level of security not only for the boot process, but also prevents unauthorized developers from accessing the firmware image itself. Increasingly this approach is becoming popular in situations where manufacturing takes place within a third-party manufacturing site.
Comprehensive support for the ConnectCore 6UL family can be found here.
Conclusion
The ConnectCore 6UL SBC provides the ideal platform from which to develop secure and trusted IIoT solutions. For some low volume applications and to establish proof of concept, the SBC can be integrated as-is. As the design is validated and production volumes grow, a custom design based around the ConnectCore 6UL SOM will assist in achieving the desired BOM goals.

Disclaimer: The opinions, beliefs, and viewpoints expressed by the various authors and/or forum participants on this website do not necessarily reflect the opinions, beliefs, and viewpoints of DigiKey or official policies of DigiKey.